Whitelist Your Mainwp Dashboard For Modsecurity
ModSecurity is a toolkit for real-time web application monitoring, logging, and access control. It is an open-source, cross-platform web application firewall (WAF) module known as the "Swiss Army Knife" of WAFs. In case you can't connect a website to your MainWP Dashboard because the ModSecurity on your child site server is blocking requests from your MainWP Dashboard, you can create a custom exception for the ModSecurity and allow your MainWP Dashboard to reach your child site. To do that,
- First, go to your MainWP Dashboard
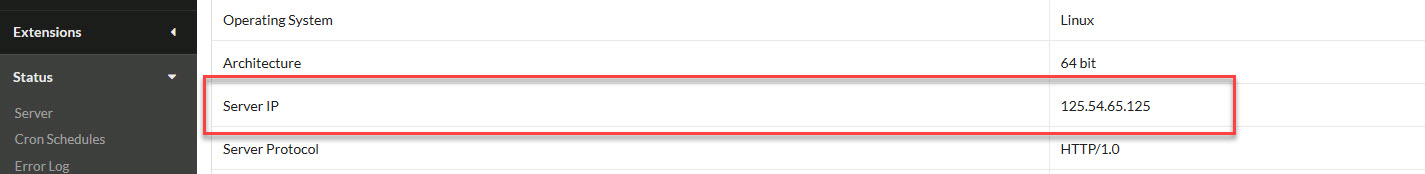
- On the MainWP > Status page, locate your MainWP Dashboard IP address and note it down.
- Now, go to your child site server and find the Nginx/Apache Error Log and find the ModSecurity error that is generated when your MainWP Dashboard tries to connect. You should be able to quickly narrow down your search with the timestamp or your MainWP Dashboard IP address. Once you’ve found your error, you need to note down the Error ID (bolded number in the example below), as we’ll be using this for our exclusion rule. It should look similar to this:
[Fri Jun 26 23:07:04.178701 2020 [:error] [pid 78007:tid 139308447686754] [client 125.54.65.125] ModSecurity: Access denied with code 403 (phase 2). Pattern match "Mozilla/(4|5)\\\\.0$" at REQUEST_HEADERS:User-Agent. [file "/etc/apache2/conf.d/modsec2.conf"] [line "109"] [id "<strong>20000221</strong>"] [hostname "127.0.0.1"] [uri "/wp-admin/admin-ajax.php"] [unique_id "WwjPWChxvG3CO5kz-D55eQBBBCU"]
- Once you have the correct ModSecurity error, you will need to edit the ModSecurity configuration. The ModSecurity configuration location can be different in different hosts, so if you are not sure where to find it, please ask your hosting provider, and they should be able to help you. Here are some examples:
- If you are using Easy Apache 4, you will find the configuration file with this path: /etc/apache2/conf.d/modsec2/whitelist.conf, if you are
- On Plesk, you will find the configuration under Tools & Settings > ModSecurity > Settings > Configuration
- If you are using Gridpane hosted sites, you will find the configuration file in /etc/nginx/modsec/owasp/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
- Open the config file and add your exclusion rule at the bottom; it should look similar to the example below, and add your MainWP Dashboard IP address and Error ID (both bolded in the example below)
SecRule REMOTE_ADDR "^<strong>125\.54\.65\.125</strong>" "phase:1,nolog,allow,ctl:ruleEngine=off,id:<strong>20000221</strong>"
- Save the changes.